|
|
1. COMPUTERS SYSTEMS - AN OVERVIEW |
Question: "What is a Computer?"
Answer: "A Computer is a machine that can store and process data.
An overview of the basic constituents of a computer, assuming a PC (Personnel Computer) configuration, is given in Figure 1.
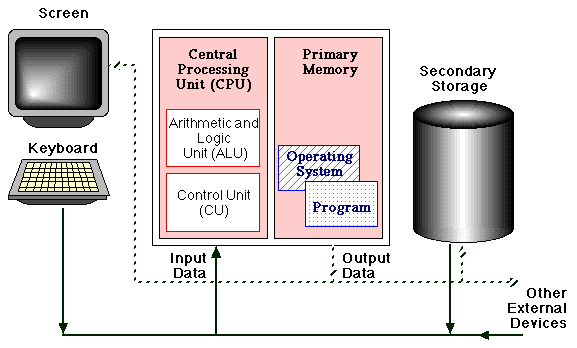
Figure 1: Constituent parts of a computer.
Points to note:
|
|
2. COMPUTER MEMORY |
|
Computer memory, primary or secondary, is composed of storage cells sometimes referred to as words. Each cell has a unique numeric address associated with it which identifies its location in the memory. The number of memory cells in a computer varies but is usually measured in millions of cells. Each memory cell contains a binary number made up of a series of binary digits or bits (binary digits), usually 8, 16, 32 or 64. This is why we sometimes use the term digital to describe a computer, i.e. a digital computer. A binary digit has two possible values 0 or 1. A binary number is therefore comprised of a sequence of 0s and 1s. The digits contained in each cell are represented by voltage levels (Figure 2), with peaks representing 1s and troughs 0s. 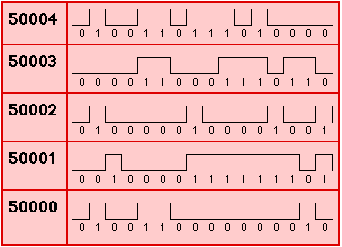
Figure 2: Computer memory organisation. A group of 8 bits is called a byte. The size of memory is usually expressed in the unit kilobyte, shortened to Kb, which is 1024 (210) bytes. Storage capacity can also be expressed as a number of megabytes (Mb) approximately a million (220 = 1048576) bytes, or gigabytes (Gb) approximately a (US) billion (230 = 1073741824) bytes. |
Despite all information being stored in the computer in a binary format, binary numbers are usually represented using hexadecimal notation (numbers to the base 16 as opposed to the base 2 used by the binary number system, or to the base 10 used in the general purpose decimal system). The hexadecimal system comprises 16 distinct digits. Hexadecimal digits 0 to 9 are the same as those for a decimal number. To represent the 6 extra digits the letters a through to f are used; these are equivalent to the decimal numbers 10 through to 15. A binary number can be converted to a hexadecimal number by partitioning the binary number into groups of four bits and evaluating each group as a hexadecimal digit. For example the binary number 0100110111010000 would be split into 0100|1101|1101|0000 which would evaluate to 4dd0 in hexadecimal form. Table 1 represents the fragment of computer memory given in Figure 2. Addresses are listed on the left, followed by a series of 16 bit words each containing binary digits. The hexadecimal and decimal equivalents are also given to the right. Note that each address is represented by a unique number - in practice this is usually a hexadecimal number. The lower end of the memory addresses range is often referred to as low memory (the other end is high memory). The operating system is normally located in low memory.
Table 1: Computer memory organisation. |
Data in secondary storage is organised into files. Conceptually a file is a named container in which a collection of data that belongs together can be stored. It might contain, for example, a program or input data for a program. Each file is given its own name so that it can be easily referred to. It is good practice to organise related files into directories and sub-directories according to (say) the nature of their application or the type of file. Use of directories allows users to organise their file store in a logical manner to prevent it from getting cluttered (more on this later).
3. COMPUTER PROGRAMS |
|
Essentially, a computer program takes some input from an input stream, translates it into some application dependent output, and sends this ourput to an output stream (Figure 3). The term stream refers to any input source or output destination. Input can be from the key board, from secondary storage or from some other external device. Output can be to the screen, to secondary storage or to some other external device. If there was no output there would be no point in having the program --- it must do something to be useful!
Figure 3: Conceptualisation of a computer program To carry out the required translation the computer program comprises a series of instructions. An instruction tells the computer that it should perform a particular task. Examples included arithmetic instructions such as addition and subtraction, and logic instructions which evaluate to true or false. One measure of a computer's performance is the number of millions of basic instructions which are performed per second (MIPS - Millions Instructions Per Second). When a program is running in a computer, it is said to be executing. At this time a copy is contained in primary memory where it occupies a number of consecutive memory cells. |
Each instruction contained in the program is stored in a memory cell (or a group of such cells) and comprises a number of bits. Different instructions are represented by different combinations of bits in the cells (currently computers cannot operate using any other form of instruction encoding). As a program executes the CU (Control Unit) reads the instructions contained in primary memory and carries them out. This will involve operations such as moving the contents of primary memory cells to the CPU (Central Processing Unit) and, if appropriate, invoking the ALU (Arithmetic and Logic Unit) to, for example, add two numbers together. The command to execute a program (regardless of the nature of the program) includes the name of the file in which the program is stored --- in many cases this is all that is required. The command causes the operating system to search for the required file in secondary memory and (if found) copy it into primary memory where it is then executed under the control of the CU. On completion control is returned to the operating system. |
4. THE COMPUTER SYSTEM WITHIN THE DEPARTMENT OF COMPUTER SCIENCE AT THE UNIVERSITY OF LIVERPOOL |
|
The Department of Computer Science at the University of Liverpool operates what is known as a distributed computer system. The resources required by the users such as software, files, memory, printers, etc. are distributed amongst a number of machines in a variety of physical locations. All the components are connected via a network which transports information and requests between any two machines on the network (see Figure 4). Thus, all resources are shared between all the users. At the time of writing the department operates what can be conceptualised as two networks: |
Both the Linux workstations and PCs provide access to a unified personal filespace, held centrally on HP series 800 UNIX file servers and backed up daily. Files can be viewed from any system within the department. |
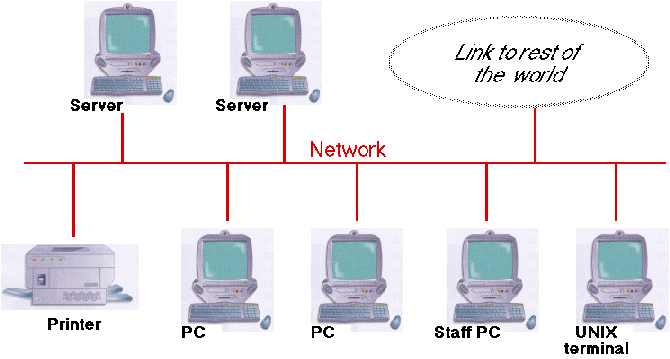
Figure 4: A distributed computer system
For further information regarding the facilities available within the department refer to the equipment section in the "Computer Science Introductory Guide".
5. SOFTWARE APPLICATIONS |
|
Software may be applied in any situation for which a previously specified set of procedural steps (i.e. an algorithm) has been defined. Potential applications include the following:
Real-time SoftwareSoftware that measures, analyses or controls real-world events as they occur in real time. Examples include plant monitoring and control systems. Business softwareBusiness information processing is the largest single software application area. Examples include payroll and stock maintenance systems. Engineering and scientific softwareEngineering and scientific software is often characterised by "number crunching" algorithms. Example applications include: astronomy, molecular biology, space shuttle orbital dynamics and volcanology. |
Embedded softwareEmbedded software is used to control products and systems for consumer and industrial markets. For example the key pad control on a micro wave oven, or fuel control in a sophisticated engine. Artificial Intelligence softwareArtificial Intelligence (AI) software makes use of non-numerical algorithms to solve complex problems that are not amenable to computation or straightforward analysis. Example application areas include: pattern recognition, theorem proving and game playing. Expert system softwareExpert systems (also known as Knowledge Based Systems or KBS) are a branch of AI. They are designed to mimic the behaviour of an expert in some well defined field. Example applications include: medicine, geology and chemical analysis. |
6. OPERATING SYSTEMS |
|
As noted in Section 1 above, apart from a program that is being executed there is always one more program permanently stored in primary memory called the operating system. This is the program (or set of programs) that is always running when no "ordinary" program is being run. Operating systems are advanced pieces of software provided by the manufacturers of computers. We say that a particular computer system "runs under" a certain operating system. Computers are designed to put the operating system directly into operation when the computer is "switched on". The operating system (amongst other things):
Some operating systems are specific to certain types of computer while others are designed to run on a range of different designs: |
We will be using two operating systems: (1) Windows' 2000(for PCs), and (2) LINUX. Using Windows' 2000 user commands are typically passed to the computer via the mouse (through clicking and dragging operations). In the case of LINUX, user commands are passed to the the computer using the keyboard. Typical commands supported by operating systems include:
Commands are simply calls to system programs which run in the same way as any other programs. |
6.1. Logging inTo begin using an operating system on a shared network such as that supported by the Department of Computer Science at the University of Liverpool you must first log in. When you login you will be prompted for your username and password. Your user name identifies you as a valid user of the system. You can not log in if you do not have a user name. Usernames are assigned by the system administrators - the people who manage the department's computer facilities. A password is an "invisible" codeword known only to its owner and helps to ensure security - it prevents unauthorised users from logging in to your file space. Again, you will initially be issued a password by the system administrators. |
To start a widows session you simply login at a PC. Instructions on how to do this will be made available to you for your first tutoraial. Once you have logged onto a PC you can start a LINUX session (UNIX) by selecting (clicking-on) the "unix session" icon that will be on your PC desk top. You will then be prersented with a list of available machines, select one of these and then log on in a similar manner to that described for starting a windows session. |
One of the first things you should do once you have got used to the logging on process is to change your password. A valid password must:
 |
Contain between 6 and 8 characters |
 |
At least two characters must be letters (upper or lower case) |
 |
At least one must be:
|
Created and maintained by Frans Coenen. Last updated 10 February 2015